I'm creating a piece of software, that will run on windows and will act like launcher for the game, to serve as an auto-updater and file verifier in client side PC.
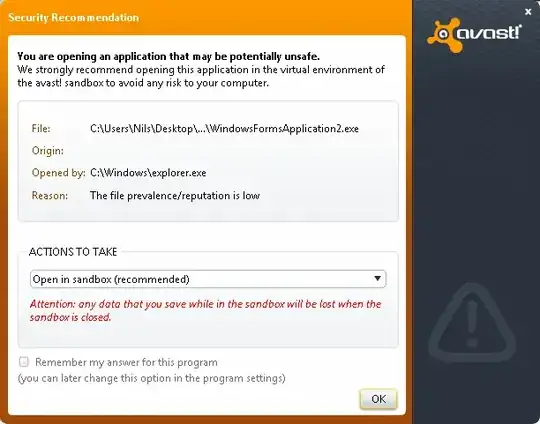
One thing I don't understand, why my antivirus software (Avast) is considering my exe file as dangerous and won't start it without asking to put it into sandbox, for safe use.
Is there any rules that my software should obey, to be treated as good, or should I pay hundreds of dollars for some sort of digital signing and other stuff?
I'm using C# with MS Visual Studio 2010.
VirusTotal report. No DLL injections, working as remote file downloader, using WebClient() class.
It is not like it warns about virus, but it "suggests" to sandbox it. Look at screenshot: