I have network situation like this:
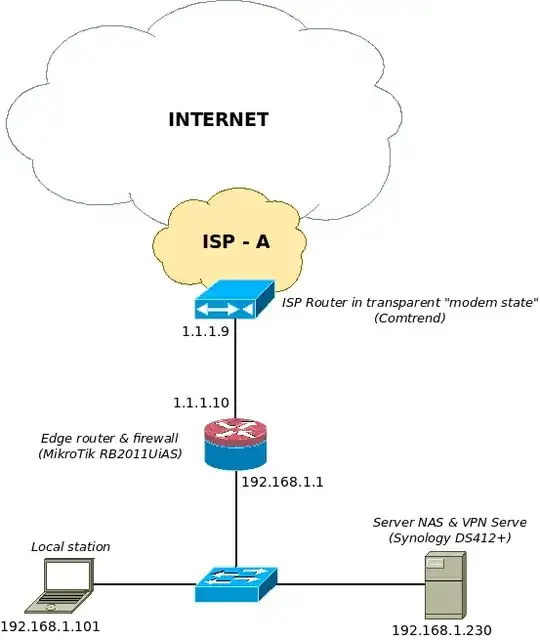
- ISP Router (modem) - device given to us by our ISP - modem & router in one but it is set into transparent mode - ISP say so ;D we have to find it that it is true :)
- MikroTik Router (MTR) - our edge router with firewall
- Server NAS & VPN Server (NAS) - Synology box with our data storage and also with VPN server with running PPTP, OpenVPN, L2TP/IPSec services- to which workers from our local company and from remote location conect to get data
- Local station (LS) - workers at our network site - they are using Windows 8 which means they use PPTP
Bellow I present our Mikrotik configuration:
Routing table:
Dst. address | Gateway | Distance | Pref. source |
0.0.0.0/0 | 1.1.1.9 | 2 | - |
1.1.1.8/30 | ether1 | - | 1.1.1.8/30 |
192.168.1.0/24 | bridge local | - | 192.168.1.0/24 |
Firewall:
Action | Chain | Dst. Address | Protocol | Dst. Port |
accept | input | 192.168.1.230 | 6 (TCP) | 1723 |
accept | input | 192.168.1.230 | 47 (GRE) | - |
accept | input | 192.168.1.230 | 6 (TCP) | 5006 |
NAT:
Action | Chain | Source Addr | Dst Address | Proto | Dst Port | Out Intf |
masquerade | srcnat | - | - | - | - | ether1 |
dstnat | dstnat | - | 1.1.1.10 | 6 (TCP) | 1723 | - |
dstnat | dstnat | - | 1.1.1.10 | 47 (GRE) | - | - |
dstnat | dstnat | - | 1.1.1.10 | 6 (TCP) | 5006 | - |
masquerade | srcnat | 192.168.1.0/24 | 192.168.1.230 | - | - | - |
The last rule is used to avoid hairpin occurrence
Rules at Mikrotik are made for now only for PPTP protocol !!!
When people from local network try connect to the VPN serwer at NAS there is error 807 or 800 occure - it deepends from station. All are Windows 8 and Windows 7. What could be the cause ?