What usb-versions do you want to support (specifically, do you need usb3)?
To answer your current question/idea:
Can I disconnect the VCC and GND wires on the sniffing cable, so that C will not try to control B?
Yes, unless your sniffer runs on the host-supplied power
Can I place a diode on the D+ or D- wires of the sniffing cable of to make the data flow only one-way?
D+ and D- are differential data (the base-voltage-levels indicate to the usb-device the maximum amount of current it may draw). So.. the diodes are useless for your application. Especially since your sniffer MUST run in 'promiscuous mode'.
Will I be able to read the data off the USB port in C?
If you build a sniffer, then yes, but not with the simple splitter-cable you have in mind.
Also note that USB3 is finally bi-directional (where as previous versions where not).
Also note that USB2 is already 480Mb/s and this might (depending on your computer C) be a lot or impossible to capture as a stream. Now USB3 will be around 5Gb/s...
So if you'd want to build a sniffer of your own, you'd be looking at a differential data buffer capable of at least 480Mb/s, and some processor to handle the copy of the data and store it in memory, then have your computer C download the captured data.
Oh, and don't forget, you'd need software on your computer do do something usefull with the captured data.
The data is encoded with NRZI. A 0 will make the signal flip sign and a 1 will keep the same signal level. If a 6bits of 1 are sended an additional 7th bit (0) is send to make the signal flip. Adding this dummy bit is called bit-stuffing and is used to keep the clocks of the host and client in sync. The clocks are generated from the data signal.
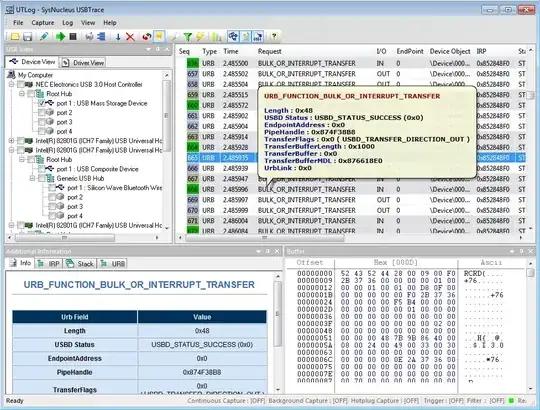
When the signal is received the NRZI is decoded and bitstuffing removed. Then the controller will detect the USB packet start (start with a synac field). The packets are buffers which are called endpoints.
CRC is applied to the packets to maintain data integrity. When an error is detected this will be flagged and the corrupt packet will be discarded.
UPDATE:
Please read this answer that details some very interesting options that might help you with software-only solutions, like in vm-ware or wireshark, depending on what information you need:
A. Physical (electrical signals)
B. The bitstream (which is just the differential between D- and D+)
C. The USB packets
D. The USB descriptors and the USB data