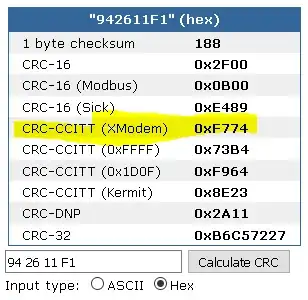
I need help identifying the checksum algorithm in the following packets please.
So, packets format is:
sd ?? dd dd dd ??
where
s = start nibble d = data (binary coded decimal) ? = unknown - possibly checksum
Here are five packets (number being transmitted in brackets) and the actual packet sent on the wire in hex on the right.
(1112694): f1 f7 11 26 94 74
(5432432): f5 7c 43 24 32 a2
(6430116): f6 dc 43 01 16 48
(3254817): f3 d8 25 48 17 e9
(0042863): f0 ce 04 28 63 b2
I've tried XOR and summing but they dont seem to work. The packets are transmitted using UART.
any help appreciated!